Protocol
Overview
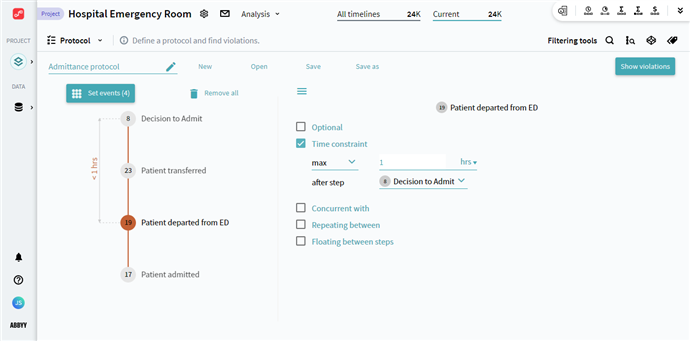
The Protocol analysis module is an instrument to make sure that the rules of a process are followed. Its main objective is to assess procedure integrity and discover deviations from expected behaviors. At a high level, it allows you to monitor the compliance of actual process instances with the requirements of a general business process. It can be also used in a more focused way, to survey the most sensitive and critical sub-processes by modeling event sequences and their patterns that are mandatory in a certain scenario. If you need to articulate any requirements, present in your actual process, in the context of Timeline, you can do it by creating a protocol. At the same time, it offers an additional possibility to create an idealized picture of a process or its parts and see how the real data differs from this ideal.
To use this analysis module, select Protocol in the drop-down list under the project's name.
The approach to monitor rule-compliance is very case-dependent, for this reason, Timeline offers an easy and straightforward set of configurations to do it. The interaction with Protocol can be divided into two simple steps:
- Create protocols to define a rule or a series of rules that should be followed in a process.
For details, see Protocol Configuration. - Discover the violations of the defined rules and investigate their reasons and outcomes.
For details, see Protocol Violations.
After this, the whole functionality of the program is at your disposal. Proceed with other analysis modules and tools to assess the outcomes of the detected violations and even find possible measures to solve the related issues.
05.09.2024 16:23:54