Protocol Violations
All the deviations from the defined protocols are detected by the program in a given timeline set and are listed in the separate Protocol violations window. To open it, click Show violations in the upper-right corner of Protocol workspace. The violations list contains the name of the event involved, the type of violation, the number of violation occurrences, and the percentage of timelines affected by it. You can filter out timelines containing a certain violation and perform a deeper analysis of them using other features of the program.
Example of Protocol violations window: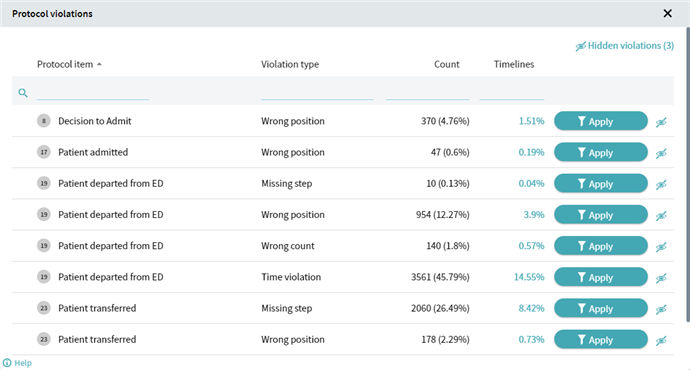
There are several types of violations:
- Wrong position
The event did not occur in a position defined by the configured sequence. It is also related to the violations of Concurrent with and Floating between steps rules. - Missing step
The event did not occur at all in timelines that contain the configured order of steps. This violation is only responsive to the sequence you set when adding events to the configuration. - Wrong count
The event occurred more or less times than it is defined by the Repeating between rule. - Time violation
The event occurred earlier or later than it is defined by the Time constraint rule.
Dealing with violations
Analyze the resulting list of violations to find their outcomes and possible causes. The actions below are offered for this purpose in the Protocol violations window:
- Hide non-critical violations.
If you believe that some detected violations are not critical for your current research, you can remove them from the main list to focus on those, that are more harmful to the process. To do it, click . Such violations can form a sub-list, to open it, click Hidden violations.
. Such violations can form a sub-list, to open it, click Hidden violations. - Review violations statistics:
- Discover how many times a pattern was violated and what percentage is the number of violation cases from the total number of the pattern occurrences in the current set.
- See how many timelines in the project contain these violations.
- Based on these observations, assess the impact of the violations on your process. Decide what cases are the most critical in terms of negative outcomes or violation frequency.
- Apply critical violations as a filter.
If you believe that certain violations are crucial for your process or occur in too many process instances, you can filter your current data set based on them. Then proceed with an analysis focused on the non-compliant timelines.
Then, you can use other analysis mechanisms offered by Timeline to investigate the possible causes of the discovered violations, find optimal methods to prevent them in the future, and monitor their occurrence in further uploads.
05.09.2024 16:23:54