Setting up Single Sign-On with Azure Active Directory
To set up SSO authentication using Azure Active Directory:
- Create and set up an application in Azure Active Directory.
a. Go to https://portal.azure.com/ and log in to your Microsoft Azure account.
b. Go to the Azure Active Directory > Enterprise applications section.
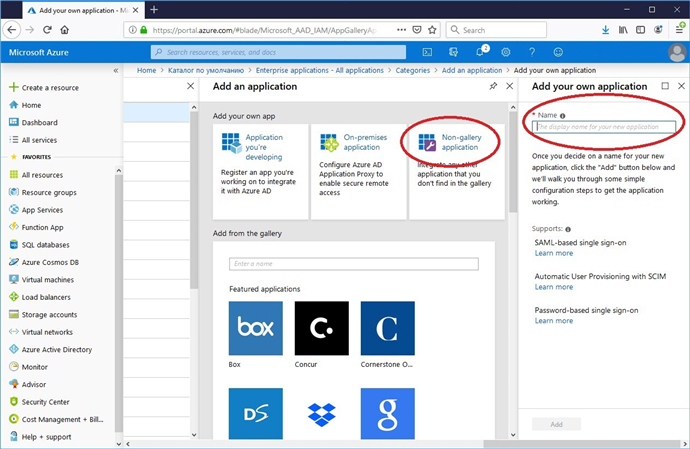
c. In the Add an application window, go to the Non-gallery application section and specify a name for the new application.
If several tenants are used, a separate application should be created for each.
d. Go to the Users and groups section and add all required users. Give them the User role.
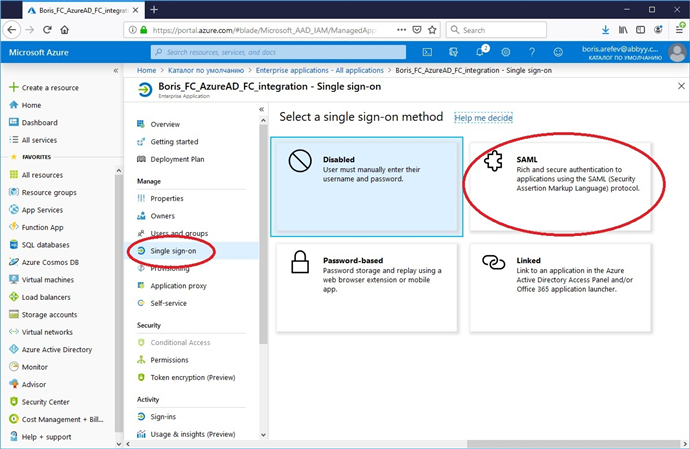
e. Go to the Single sign-on subsection and select SAML.
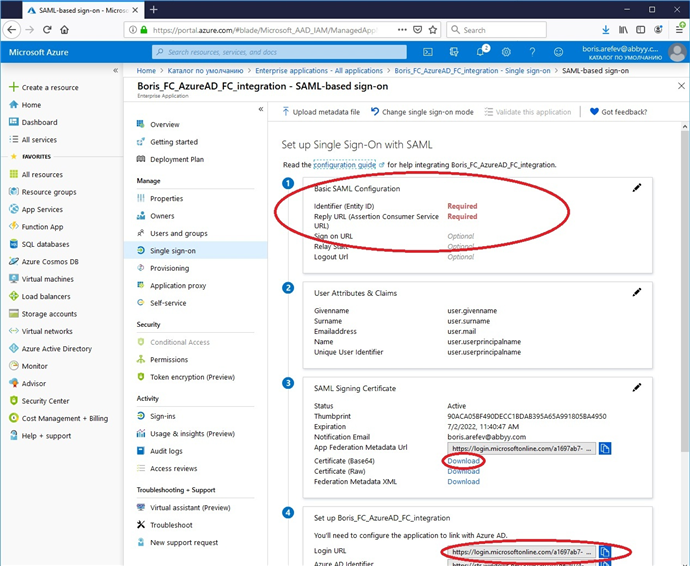
f. Edit the Basic SAML Configuration section as follows:
Specify the Identifier (Entity ID) and the Reply URL (Assertion Consumer Service URL) in the respective fields:
https://<app-server-dns-name>/FlexiCapture12/Login/AccessToken/Saml
 Note: When setting up a tenant, URLs should be specified in the following format: https://<app-server-dns-name>/FlexiCapture12/Login/<TenantName>/AccessToken/Saml
Note: When setting up a tenant, URLs should be specified in the following format: https://<app-server-dns-name>/FlexiCapture12/Login/<TenantName>/AccessToken/Saml
Leave the rest of the fields blank.
- In the SAML Signing Certificate section, download your public certificate in Base64 format by clicking the link next to Certificate (Base64).
- From the Login URL field in the Set up [application name] section, copy the URL for accessing the server of the external identity provider.
- Set up the required parameters in ABBYY FlexiCapture using a script. To do this:
a. Download the script here.
b. On the machine where ABBYY FlexiCapture is installed, open the Windows PowerShell console as an administrator.
c. Specify the script name, the path to the script, and the following parameters:
- the path to the Application Server
- the path to the public certificate
- the path to the image that will be used for the new button (images in *.svg, *.jpg, and *.png formats are supported)
- the name of the tenant for which the parameters are being set up
- the name of the external identity provider that will be contacted when the user clicks the Log in with… button
- the URL that will be used to access the server of the external identity provider
Below is a sample command that runs the script.
C:\Temp\SetIdentityProvider.ps1 /url 'https://localhost' /certFilePath C:\Temp\AzureAD_FC_integration.cer /pictureFilePath 'C:\Temp\index.svg' /tenant 'TenantName' /providerName 'Azure AD' /pictureFilePath 'C:\Temp\index.svg' /Reference 'https://login.microsoftonline.com/123e4567-e89b-12d3-a456-426655440000/saml2'
In this sample command:
a. url is the path to the Application Server,
for example, $url = 'https://localhost'.
b. certFilePath is the path to the public certificate,
for example, $certFilePath = 'C:\Temp\AzureAD_FC_integration.cer'.
c. pictureFilePath is the path to the image that will be used for the new button,
for example, $pictureFilePath = 'C:\Temp\index.svg'.
d. tenant is the name of the tenant for which the parameters are being set up,
for example, $tenant = 'TenantName'.
 Note: This parameter should only be specified if multiple tenants are used.
Note: This parameter should only be specified if multiple tenants are used.
e. providerName is the external identity provider,
for example, $providerName = 'Azure AD' (the button text will then say "Log in with Azure AD").
f. Reference is the URL for accessing the external identity provider,
for example, $Reference = 'https://login.microsoftonline.com/
123e4567-e89b-12d3-a456-426655440000/saml2'.
As a result, the following button will appear on the web station's login page: Log in with Azure AD.
 Note: For more technical details about SAML authentication requests and responses that Azure Active Directory supports for Single Sign-On, please refer to this article on Microsoft.com.
Note: For more technical details about SAML authentication requests and responses that Azure Active Directory supports for Single Sign-On, please refer to this article on Microsoft.com.
4/12/2024 6:16:01 PM